I tend to be a bit paranoid so went ahead and pushed the blocking registry keys out on those clients with WSUS anyway . . .
According to Microsoft you can block this upgrade entirely on all workstations on your network, as well as turn off the nagging upgrade popup/notification, with two registry key additions.
If you are running a Domain Controller / Active Directory you can push these simple registry keys to all computers under that server. Alternately you can download and install an update on the AD Server and push the same settings out with a new template. I chose to use the simple approach for now.
More information from Microsoft on these settings (and how to later reverse them) is on their knowledge base article: How to manage Windows 10 notification and upgrade options.
Note: the following method requires that workstations running Windows 7 have the March 2016 Windows Update Client - kb3138612 at a minimum. Newer Update Clients also work. Older ones will not "see" the registry keys below and may still be upgraded fully to Windows 10 by accidentally clicking the wrong thing.
The two keys we want look like this - and you can manually import these into any workstation running Windows 7 or 8.1 to prevent upgrades - no domain needed.
Important! Note the Odd CaPitaliZation on the keys below - they must be entered exactly as shown.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\GWX]
"DisableGwx"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate]
"DisableOSUpgrade"=dword:00000001
To push these out via Group Policy:
1) on the domain controller server open the Group Policy Management console.
2) for our purposes we will Edit the Default Domain Policy
3) navigate to Computer Configuration, Preferences, Windows Settings, Registry
4) right click Registry and select New, Registry Item
5) Create an Update rule for HKEY_LOCAL_MACHINE
with Keypath: SOFTWARE\Policies\Microsoft\Windows\GWX
and Value: DisableGwx
And Type: REG_DWORD
and Value Data: 1
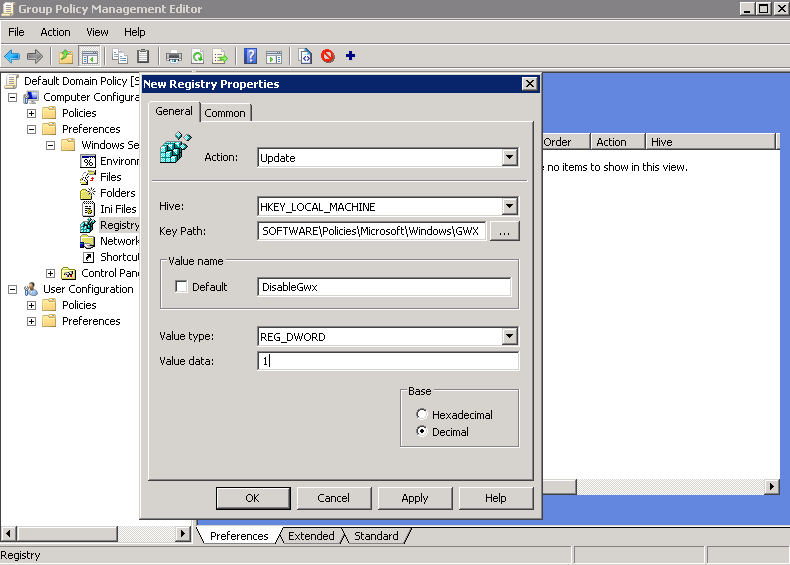
Click OK and lets do the second key!
6) Same place - right click Registry and select New, Registry Item
7) Create an Update rule for HKEY_LOCAL_MACHINE
with Keypath: SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate
and Value: DisableOSUpgrade
And Type: REG_DWORD
and Value Data: 1

Here's what you should see when you check your work (right click the below image and View to see it all)

And here is the test on a client machine after forcing a Group Policy update:


Remember to reboot all the clients - this policy is delivered during startup of the target machine, also reboot if you manually applied these registry keys.
Cheers!