If you manage an older Office 365 tenant, and noticed that your old MFA settings and other security features stopped working, you might have read that there are a new set of security baseline settings available.
However . . . when you attempt to enable those settings, the Azure admin portal fails to accept them with various errors. Other features that may break include turning on new polices for safe links, safe attachments, or anything to do with legacy authentication or MFA enforcement.
A quick test: try to follow the steps in this Microsoft document:
https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-security-defaults
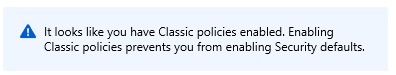
When you click the link on your portal under Properties >> Manage security Defaults and try to turn on "Enable Security Defaults" you may see this failure error message:
Worse, if you are using the "Free" version of Azure without a P1 license or higher, you can no longer navigate via the menu to the classic policies to audit them. So (as of this writing) here is a direct link to the page you need:
https://portal.azure.com/?microsoft_aad_iam_classicPolicyDontHide=trueµsoft_aad_iam_enableClassicPoliciesMenu=true#view/Microsoft_AAD_IAM/ConditionalAccessBlade/~/ClassicPolicies
There, you will see a page much like this, with four or more policies enabled. Click the triple dot option link beside each and disable.
Back at your policy page, do a forced refresh and try to enable the Security Defaults again, it should work now!

No comments:
Post a Comment
Comments are welcome but moderated to prevent spam links. I usually check them at least once a day in the evenings - so please be patient with me if your comment does not appear quickly.
Thank you.